1. Overview
By default, only a few components of BEXIS2 are accessible for anonymous users. Any further access to the application is available for authorized users, only. Therefore, Administration module provides probably of user registration that could control by administrators. After a successful registration, user is able to logon to BEXIS2 using its account credentials for authentication.
2. RegistrationRegistration is accessible through the menu bar. All fields are mandatory and system needs accept of the Terms and Conditions. To complete successfully the registration process you need to react to a confirmation Email.
2.1. LoginFirst, press Login button. The system redirects you to the login form and you have to enter your account credentials (user name and password). If the login is successful, you will see Dashboard. Otherwise, the system will notify you about the status and reason why the logon was not successful.
3. UsersCaution! This part of the system is secured. You may not have access to it. BEXIS2 provides different features for managing users. These are typically available to system administrators only. Each of them is described in more detail in one of the following subsections.
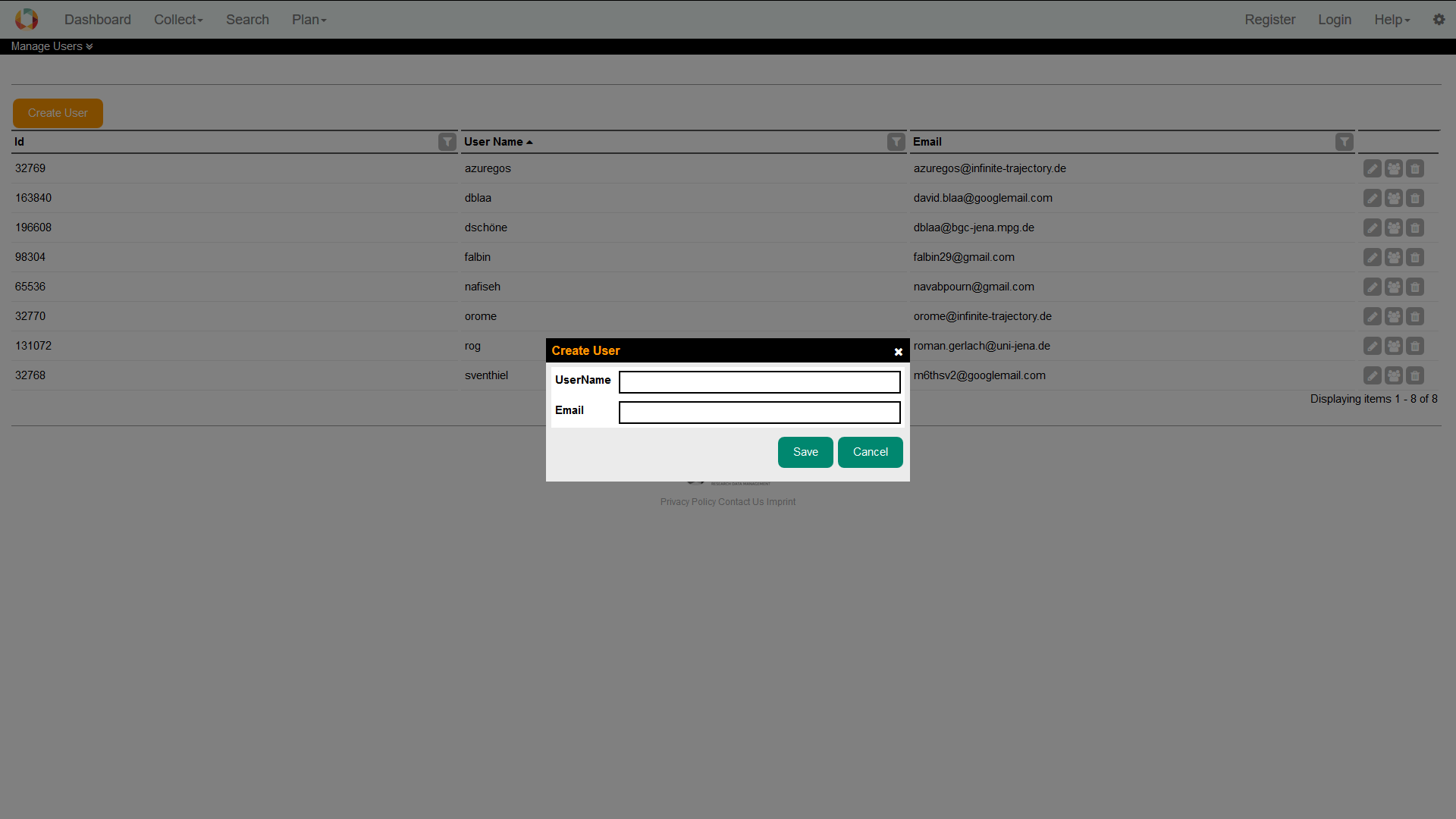
3.1. Create a userIn addition to the self-registration procedure, user accounts may also be created by an administrator. This feature is available from Setup > Manage Users. Please press the Create button. A modal window will pop up that contains the user creation form. Similar to the self-registration, the system supports you with validation on all information entered.
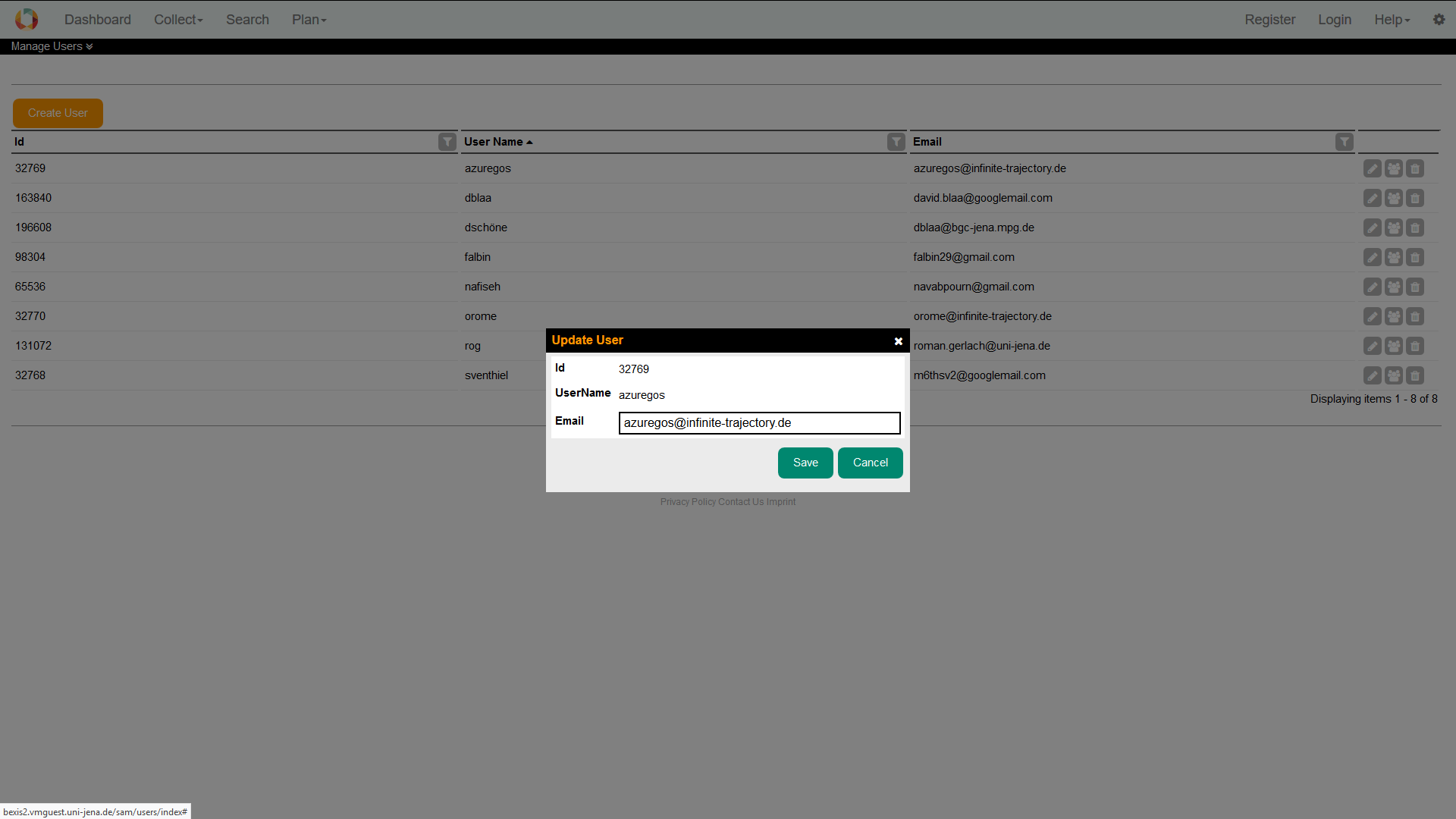
3.2. Edit a userWithin BEXIS2 you are able to display and modify user information. For security and usability reasons, the system allows modification only for certain parts of the user information. Please go to Setup > Manage Users and press the Edit button of the respective user. You are now able to alter the user information. Changes are committed to the system when you press the Save button. For any given user memberships to certain groups need to be specified via the tab Membership. You can change the status easily by (un)select the corresponding checkbox.
4. GroupsCaution! This part of the system is secured. You may not have access to it. BEXIS2 provides different features for the managing groups. They are typically available to system administrators only. Each of them is described in more detail in the following subsections.
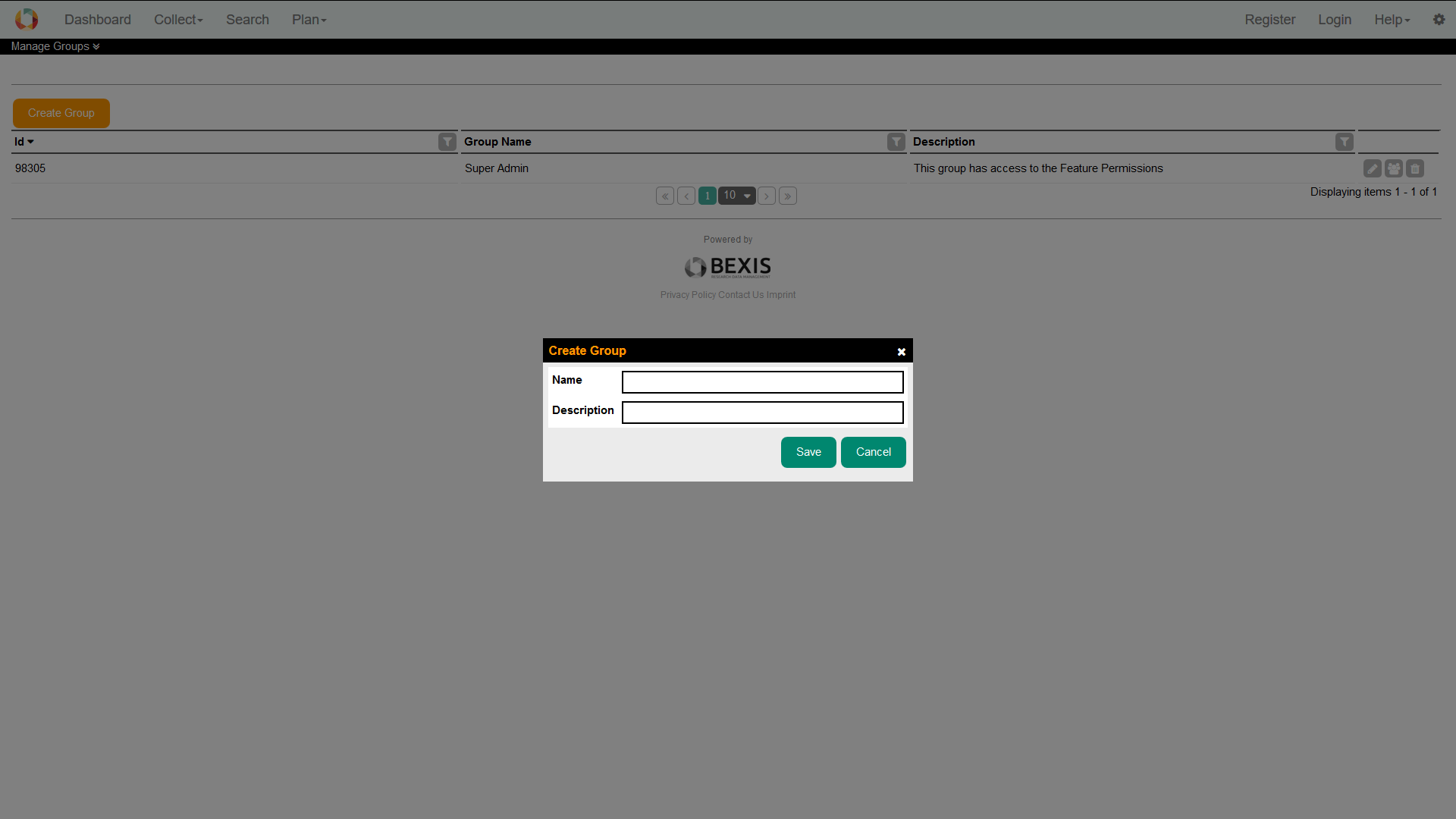
4.1. Create a groupThis feature is available from Setup > Manage Groups. Please press the Create button. A modal window will pop up that contains the group creation form. The system supports you with validation on all information entered.
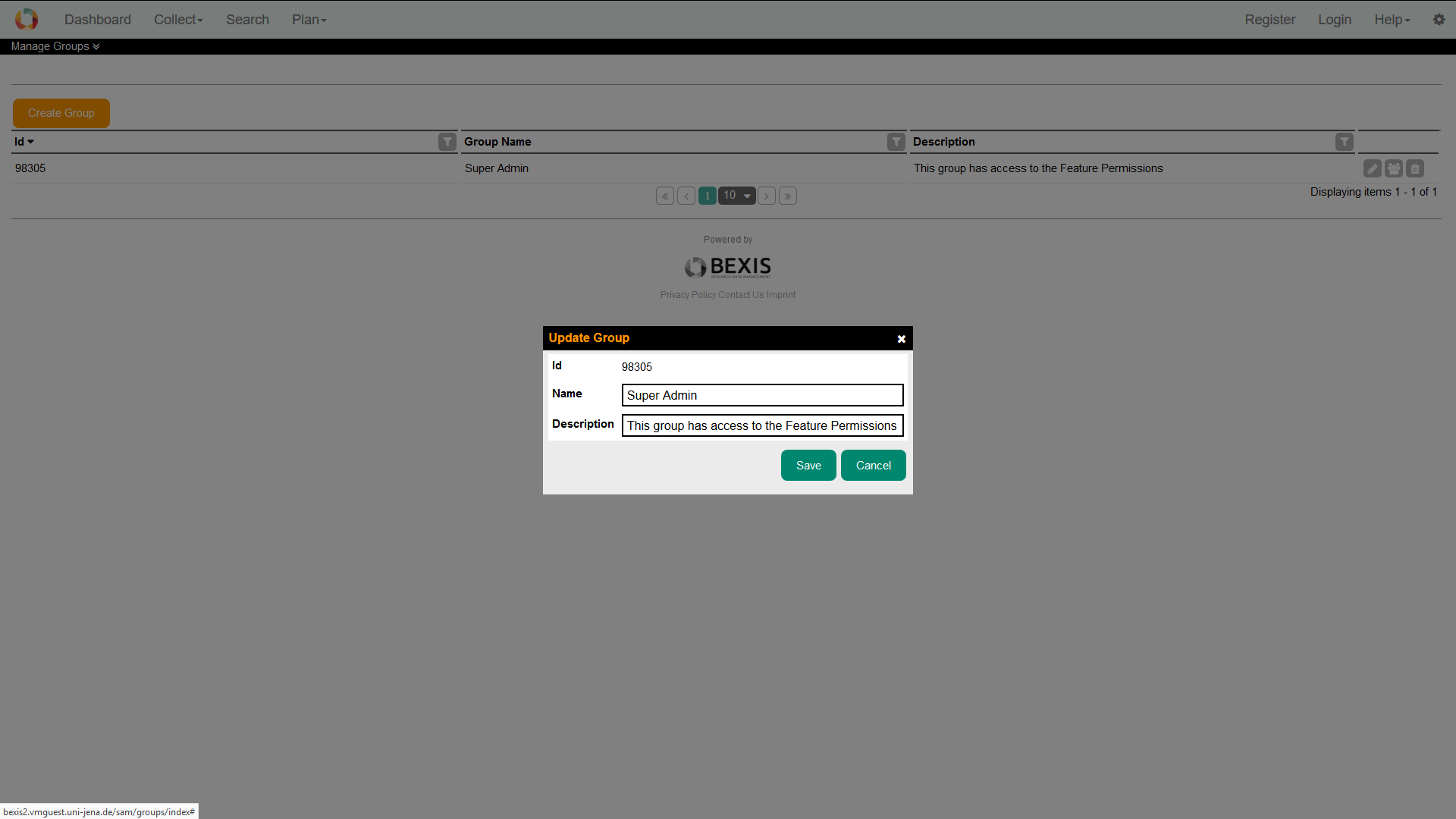
4.2. Edit a groupWithin BEXIS2 you are able to display and modify group information. Please go to Setup > Manage Groups and press the Edit button of the respective group. You are now able to alter the group information. Changes are committed to the system once you pressed the Save button. For any given user memberships to certain group need to be specified via the tab Membership. You can change the status easily by (un)select the corresponding checkbox.
5. PermissionsCaution! This part of the system is secured. You may not have access to it. Permission is a rule that contains certain security regulations. In general, it is possible to set a rule on both, users and groups. The security system of BEXIS2 distinguishes between two types of permissions. On the one hand, there are feature permissions, which allow or prohibit the access to well-defined and delimited areas of the application. This type of permissions is working on functional objects (e.g. actions that should be performed) - so called Features. On the other hand, data permissions provide the ability to protect real data (e.g. datasets, research plans and so on).
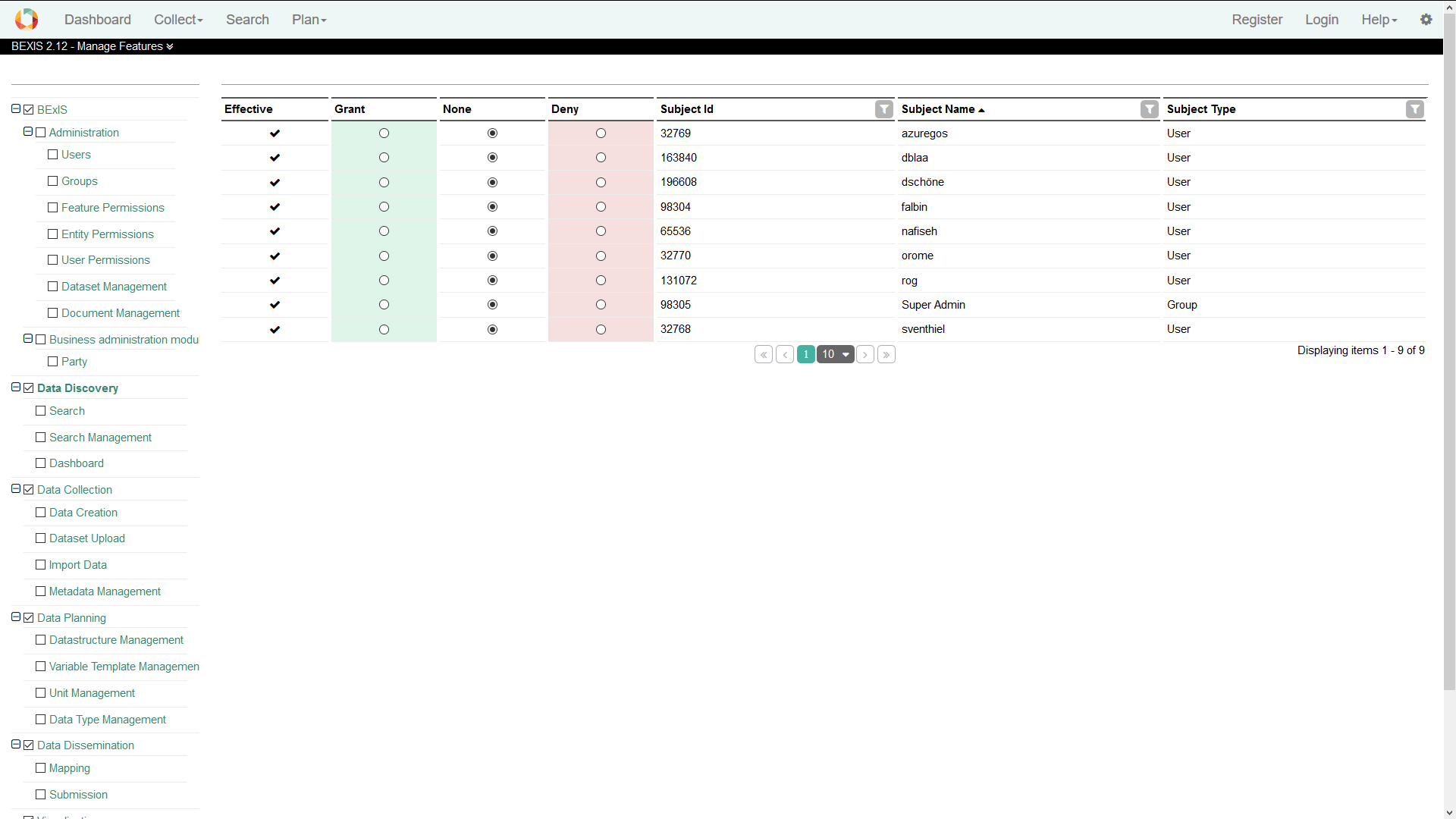
5.1. Feature PermissionsTo be able to modify features, Please go to Setup > Manage Feature Permissions. This will bring up a page with a tree on the left side. Selecting a checkbox in the navigation tree (e.g. Search) will make that feature accessible without authentication (public access). Please use with care! By clicking a feature name (a node in the tree), the system will show a table on the right side (see below). This table contains all subjects (users and groups) and their feature permission status. You may grant or deny permissions for individual users or groups using the radio buttons. If a permission is not explicitly set (i.e None) permissions are inherited from up level features. Inherited permissions are shown in the first column as effective permissions.
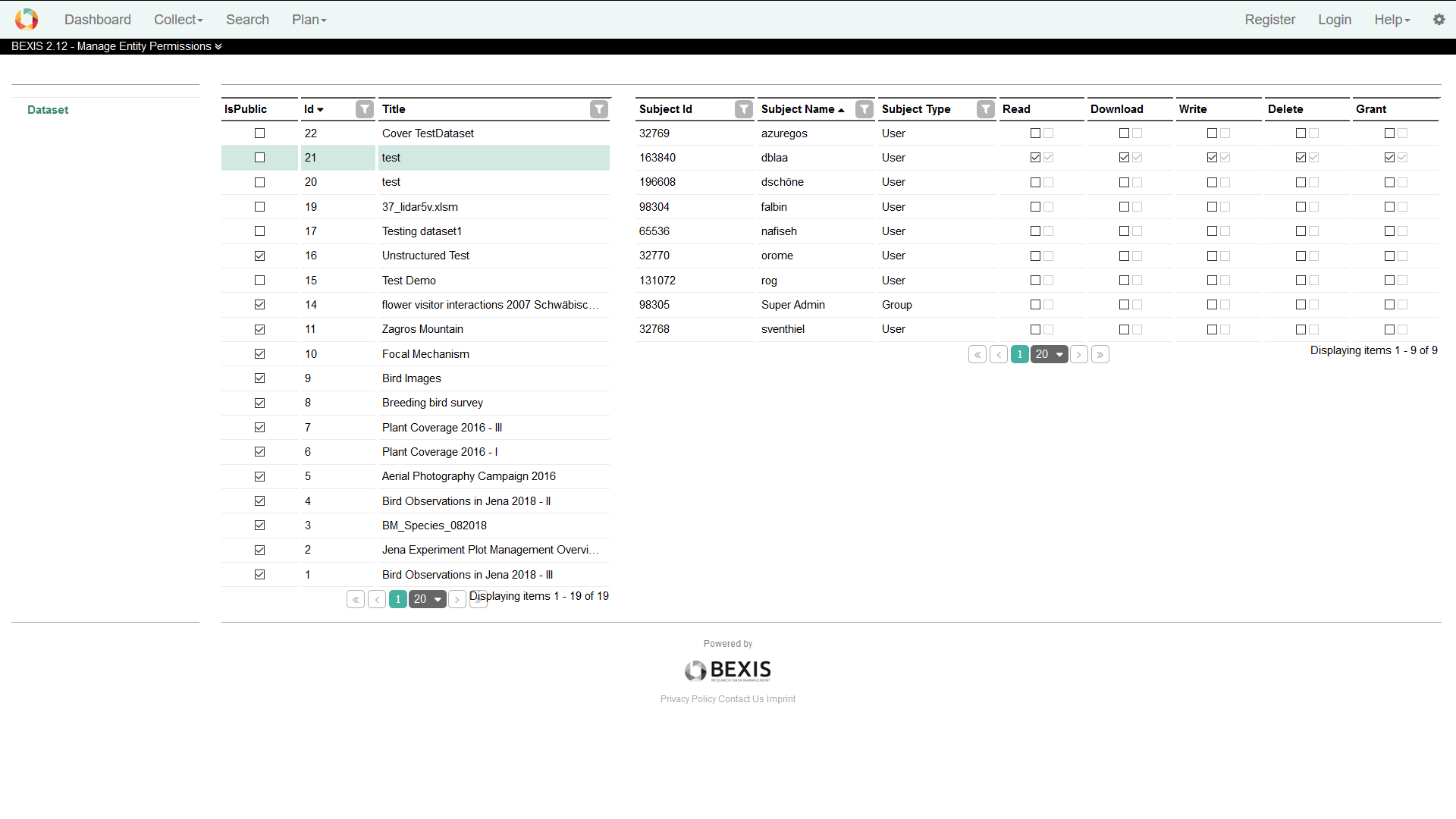
5.2. Entity PermissionsThe security system of BEXIS2 is working on both, functional (features) and non-functional (entities) items. Please go to Setup > Manage Entity Permissions if you like to manage access to entities (datasets). By selecting a dataset (i.e. a row in the table), the system will show a second table underneath the first one, which contains all subjects (users and groups) and their different data permission statuses regarding the selected dataset. On this page, you are also able to alter the different kinds of data permissions for a selected dataset. Selecting the checkbox in the first column (i.e. IsPublic) will allow public access to that dataset without any authentication.
In general, the system works on six different data permission types:
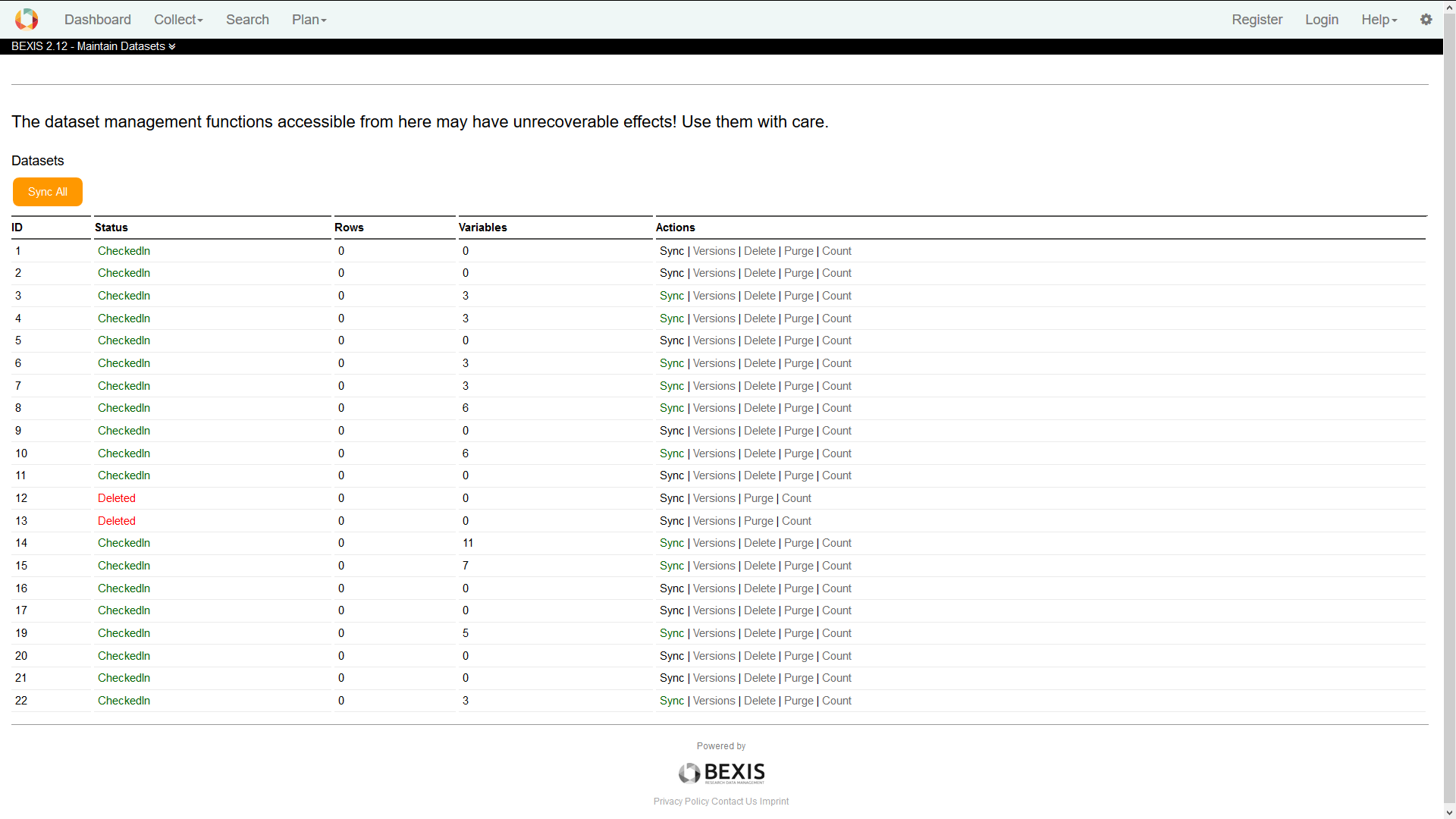
6. Manage DatasetsVia menu in Setup > Manage Datasets you are able to see a list of Datasets. In this list you can see the status of each dataset and some useful actions for the maintenance of a dataset.
There are two ways to delete a dataset: Delete: this function tags a dataset to exclude it from nearly all features of the system (e.g. search). But the dataset itself will stay inside the database. So later on you are able to recover the dataset - if needed. Purge: the dataset will be removed from the system at all (incl. removal of data permissions, metadata and primary data). There is no way to rollback that action. Note that if you purge a dataset, you cannot recover it at all.
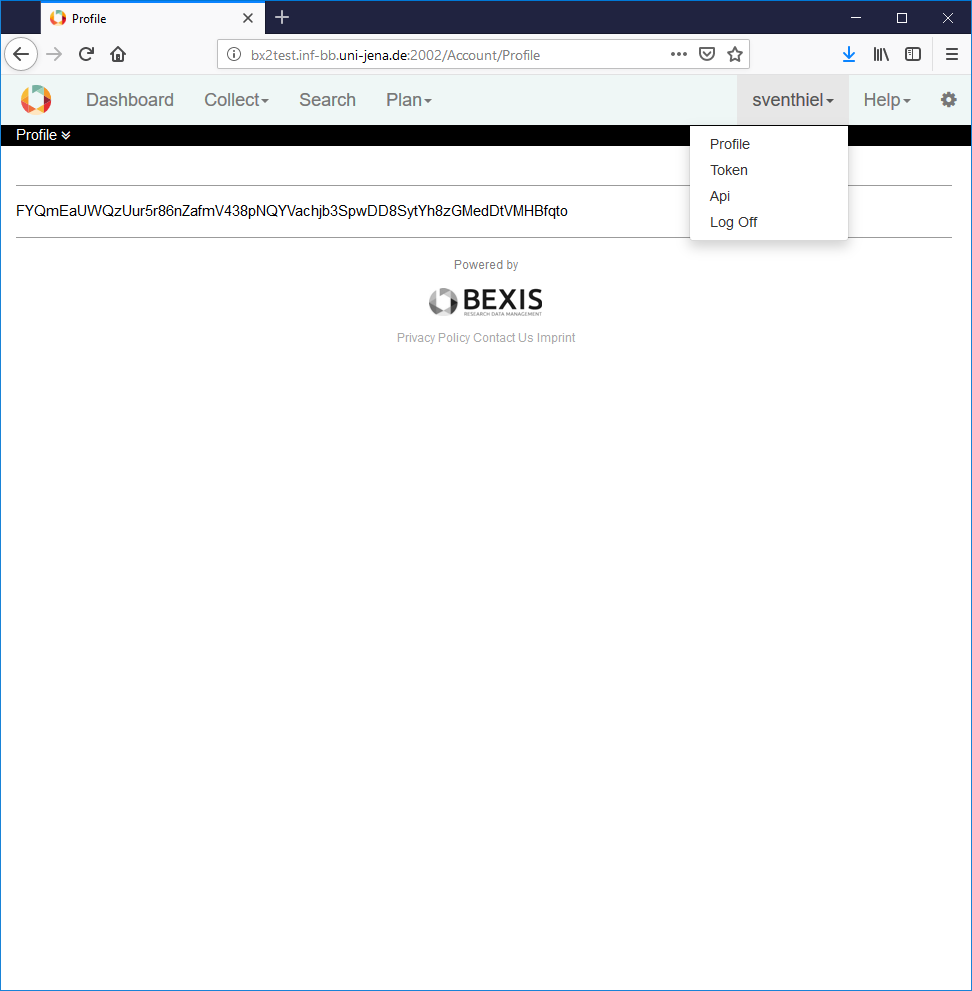
7. API TokenIn general, the APIs of BEXIS2 are protected by both mechanisms, authentication and authorization. In contrast to the login where usual credential are used, the APIs are using a personalized token for authentication. Within the user menu, each user has the possibility to show her/his own token. Afterwards, that token can be used for the APIs.
Go to top |